The Crucial Role of Zero Trust Security in 2025: Implementation Strategies for a Safer Digital Landscape
CYBERSECURITY
Bryan Solidarios
7/14/20255 min read
Understanding Zero Trust Security
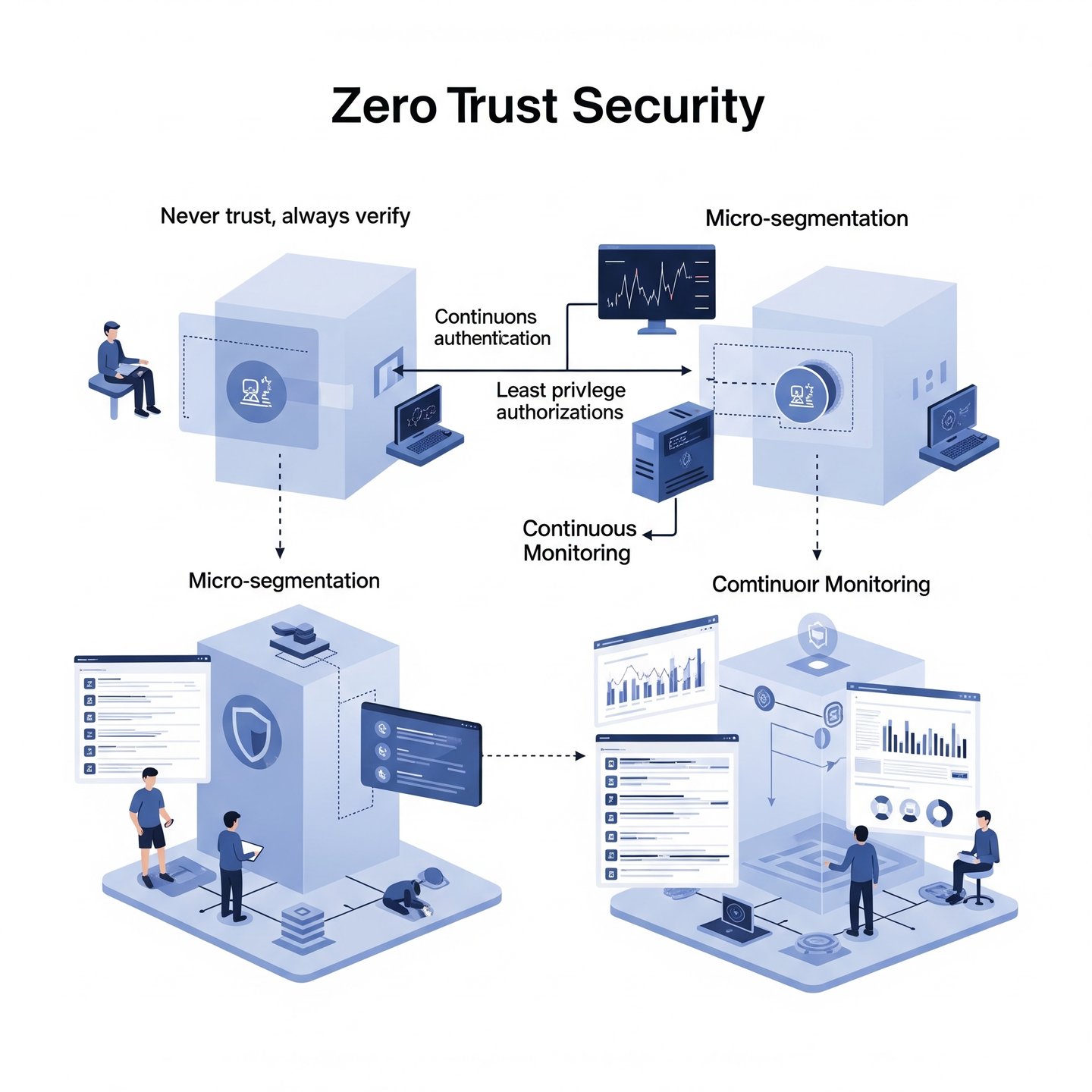
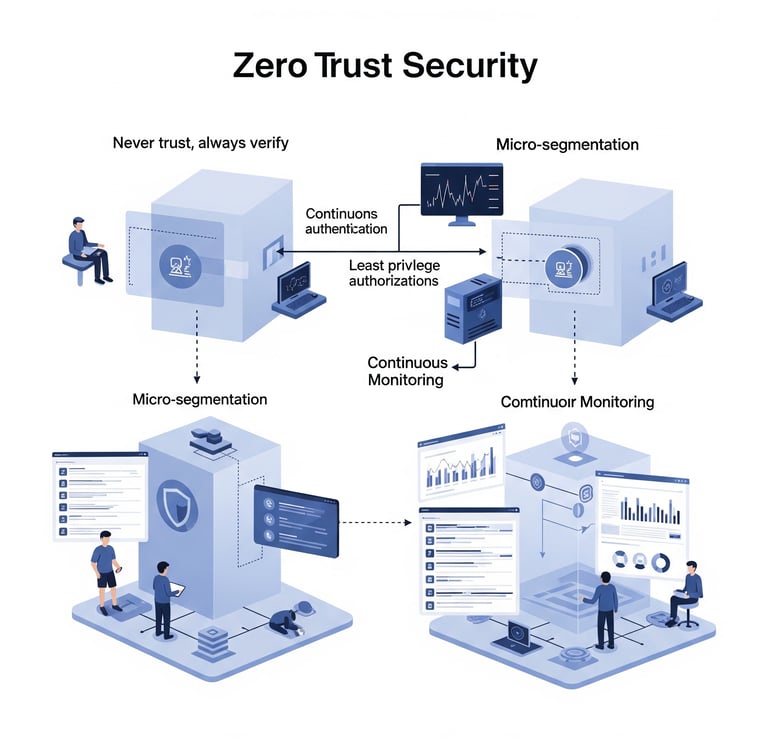
Zero Trust Security is a modern cybersecurity framework that fundamentally reshapes how organizations think about security in an ever-evolving digital landscape. Unlike traditional security models that accept users within a network as trusted by default, the Zero Trust approach operates under the principle of “never trust, always verify.” This paradigm shift means that every access request is treated as a potential threat, regardless of its origin.
At the core of the Zero Trust model are several key tenets designed to enhance security posture and mitigate risks associated with modern cyber threats. One such principle is least privilege access, which ensures that individuals or systems only have the minimum level of access necessary to perform their tasks. This concept is crucial in minimizing damage in the event of a security breach, as it limits the capabilities of malicious actors who may gain unauthorized access.
Another vital component of Zero Trust Security is micro-segmentation. By dividing networks into smaller, isolated segments, organizations can create barriers that significantly increase the difficulty for threats to traverse the entire network. Should a breach occur within one segment, the lateral movement of threats can be effectively contained, allowing for quicker response and remediation efforts.
Additionally, continuous monitoring and validation of users’ identities and devices are central to the Zero Trust framework. Organizations employ advanced authentication methods, such as multi-factor authentication (MFA), to constantly verify users, even after they have logged into a system. This ongoing scrutiny forms a critical defense line against persistent advanced threats and ransomware attacks.
Overall, implementing a Zero Trust Security model empowers organizations to safeguard their digital assets by addressing vulnerabilities more effectively and adapting to the changing nature of cybersecurity threats.
The Growing Necessity of Zero Trust in 2025
As we move towards 2025, the landscape of cybersecurity threats continues to evolve at an alarming pace. The increasing sophistication of cyber attacks, coupled with advanced technology, creates an environment where organizations must reassess their security strategies. Traditional measures, which often rely on perimeter-based defenses, are no longer sufficient to safeguard sensitive information and critical infrastructures. This shift necessitates the adoption of a Zero Trust security model.
Remote work has fundamentally altered how businesses operate, resulting in a broader attack surface. Employees accessing corporate resources from various locations and devices expose organizations to potential vulnerabilities. In addition, the rise of cloud computing has facilitated unprecedented efficiency and scalability, yet it also introduces new risks, as sensitive data is stored and accessed across multiple platforms. The Internet of Things (IoT) devices, which are increasingly integrated into both personal and professional environments, further complicate the cybersecurity landscape. These devices often lack adequate security mechanisms, making them attractive targets for attackers.
In this context, a Zero Trust model—which operates on the principle of “never trust, always verify”—is pivotal. By assuming that threats could originate both inside and outside the network, this approach requires continuous authentication and validation of users and devices before granting access to resources. It emphasizes micro-segmentation, ensuring that even if a breach occurs, the lateral movement within the network is considerably limited. The Zero Trust framework not only enhances visibility into who is accessing what but also helps organizations to respond swiftly to any threats, thus bolstering their overall cybersecurity posture.
Given the dynamic threat environment and the increasing complexity of enterprise networks, implementing Zero Trust principles is not just an option—it is an imperative for organizations wishing to maintain security and protect their assets in 2025 and beyond.
Implementing Zero Trust Security: A Step-by-Step Guide
As organizations increasingly acknowledge the significance of cybersecurity, implementing Zero Trust Security has become paramount. The Zero Trust model fundamentally redefines security protocols by operating under the premise that threats can be both external and internal. This approach requires a comprehensive strategy that encompasses various vital steps for effective implementation.
First and foremost is asset identification. Organizations should begin by cataloging all physical and digital assets, including hardware, software, and data repositories. Understanding what needs protection lays the groundwork for a robust Zero Trust architecture. This inventory enables security teams to prioritize assets based on their sensitivity and importance to overall cybersecurity.
The second step involves user authentication processes. Organizations must implement stringent authentication methods that ensure only legitimate users can access sensitive data. Multi-factor authentication (MFA) is a crucial component of this step, adding a layer of security that significantly decreases unauthorized access risks.
Next, access controls must be established. This involves defining user roles and assigning permissions based on the principle of least privilege, ensuring that users have only the access necessary for their roles. Continuous evaluation of these permissions is essential to maintain a secure operating environment.
Continuous monitoring of network activity is another critical aspect of a Zero Trust framework. Organizations should utilize advanced analytics and machine learning to monitor user behavior and detect anomalies that could indicate potential security threats. This proactive approach allows for quicker response times and mitigates potential risks.
Finally, incident response planning cannot be overlooked. Organizations must develop and regularly update an incident response plan tailored to the Zero Trust model, ensuring that all stakeholders understand their roles during a cybersecurity event. Integrating these security measures into the organization’s culture and daily operations fosters a holistic approach to security, involving every team member in achieving a safer digital landscape.
The Future of Zero Trust Security: Trends and Innovations
The evolution of cybersecurity strategies has led to the increasing adoption of Zero Trust Security models, which assume that threats could be internal or external. As we look toward the future, several trends and innovations are likely to shape the development of Zero Trust implementations significantly. One of the foremost trends is the integration of artificial intelligence (AI) and machine learning into Zero Trust architectures. These technologies can enhance threat detection and response capabilities, enabling organizations to identify anomalies and potential breaches more effectively. By analyzing large amounts of data, AI can optimize security protocols, making them more responsive and effective.
Another essential aspect of the future of Zero Trust is automation. The deployment of automated security solutions can streamline the management of access controls and user permissions. As the complexity of IT environments increases, automated tools can reduce the burden on IT security teams, allowing them to focus on more strategic challenges. Automation in cybersecurity can lead to real-time adjustments to security policies based on user behavior, enabling a more dynamic approach to risk management within Zero Trust frameworks.
Moreover, as regulatory landscapes evolve, organizations implementing Zero Trust strategies may face new compliance requirements. Authorities worldwide are emphasizing data privacy and protection, leading to stricter regulations that could impact security practices. This growing emphasis on compliance will require organizations to adapt their Zero Trust frameworks to meet these new standards, ensuring that they protect sensitive information while remaining compliant with laws and regulations. In addition to traditional industries, sectors such as healthcare and finance will need to prioritize Zero Trust principles, focusing on safeguarding data and minimizing breaches.
In conclusion, the future of Zero Trust Security will be shaped by the integration of innovative technologies and the adaptive nature of compliance requirements. Organizations must stay ahead of these trends to create a robust cybersecurity posture in an increasingly complex digital landscape.
For any concerns, suggestions, feedback, please contact us at support@bryansolidarios.com
© 2025. All rights reserved.
Subscribe here
AI Assistant
AI Content & Licensing Disclosure
All musical tracks and visual media under the "System Failure" project are created using a hybrid of human composition and Advanced Generative AI (Suno v5/v2026 & Image Generation).
Commercial Rights: All tracks hosted here are generated under an active commercial license.
Ownership Note: Per 2026 AI platform terms, while commercial use is granted to Bryan Solidarios, the copyright status of AI-generated outputs is subject to evolving international laws regarding non-human authorship.
Educational Purpose: This content is part of a cybersecurity awareness initiative to demonstrate the intersection of IT, AI, and digital security.