How Secure Is Your Password?
how criminals can crack passwords and how to protect oneself from such attacks
Bryan Solidarios
7/26/20258 min read


The Password Puzzle: Unmasking How Criminals Crack Your Codes & Your Blueprint for Digital Safety!
Hey everyone! Our digital lives are built around secure access to personal information, making passwords essential for safeguarding our online presence. But have you ever paused to think about how easily those keys could fall into the wrong hands? It might sound like a scene from a spy movie, but the reality is that cybercriminals have become quite skilled at figuring out our digital secrets.
The good news is that understanding how these criminals operate is the first and most powerful step towards protecting yourself. So, let’s demystify the world of password cracking and arm you with practical tips to build an impenetrable digital vault and protect yourself from such attacks!
Decoding the Hacker's Playbook: Sneaky Ways Criminals Crack Your Passwords
The days of hackers simply guessing your password are gone. Today's cyber attacks are often sophisticated and automated. Here’s a peek into some common techniques criminals use to crack passwords:
1. Brute-Force Attacks: The Relentless Number Game
Imagine a super-speedy robot trying every single possible combination of letters, numbers, and symbols until it stumbles upon your password. That’s essentially a brute-force attack. Modern technology allows these automated systems to make billions of attempts every second!
A Quick Story: Think of it like trying to open a combination lock with a million possible combinations. A human would take forever, but a computer program can try them all incredibly fast. If your password is short and uses common characters, it’s like having a simple combination on that lock.
Your Vulnerability: Short, simple passwords are the easiest targets for this. This is a key point to remember for password tips.
2. Dictionary Attacks: Exploiting Our Predictable Choices
We humans tend to choose passwords that are easy to remember – common words, names, dates, or simple sequences. Dictionary attacks exploit this human tendency.
How it Works: Attackers use massive lists (or "dictionaries") of common words, phrases, names, popular terms, and even common password variations (like replacing ‘o' with ‘0’ or 'a' with ‘@’). Their software rapidly tries these against your login.
Practical Example: If your password is “Sunshine2024!”, while it might seem okay, “sunshine” is a dictionary word, and “2024” is an obvious year. A dictionary attack, possibly combined with simple substitutions, could figure this out relatively quickly. These are important crack tips to be aware of.
3. Credential Stuffing: The Danger of Reusing Keys
This is a widespread and dangerous attack that capitalizes on a common bad habit: using the same password across multiple websites and apps.
The Domino Effect: Imagine a less secure website you used years ago gets hacked. Your username and password from that site end up on the dark web. Criminals use these stolen credentials to hack your other important services like email, banking, and social media. If you used the same password, they now have access to those accounts too!
Real-World Impact: Think of it like having the same key for your house, your car, and your office. If a thief gets that one key, they have access to everything. That’s the risk with reusing passwords. This highlights why unique password tips are crucial.
4. Phishing & Social Engineering: Tricking You to Give Away Your Keys
Sometimes, the easiest way for criminals to get your passwords isn't by hacking them, but by simply tricking you into revealing them. Phishing attacks are deceptive tactics designed to manipulate you.
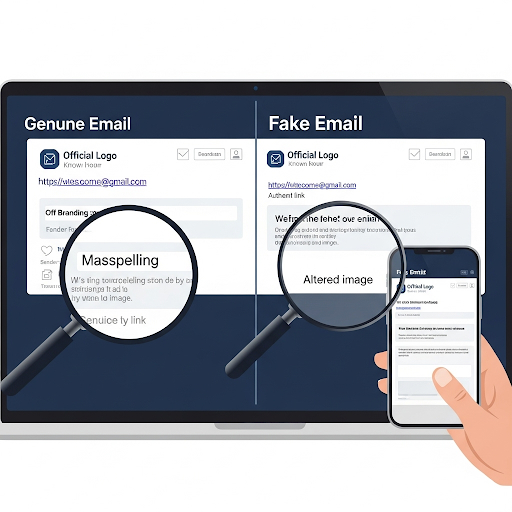
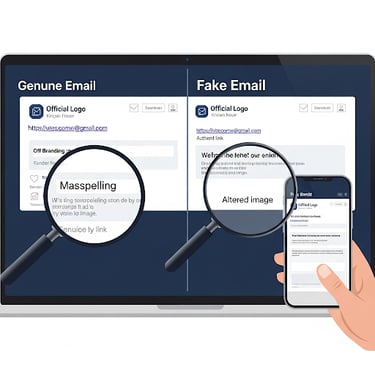
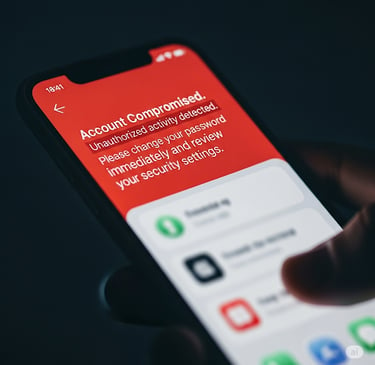
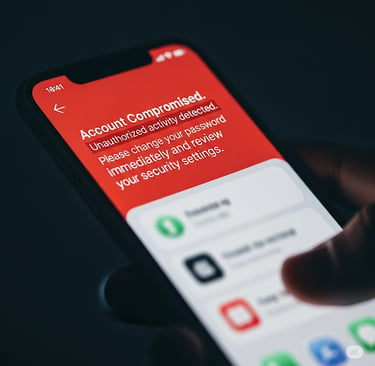
The Bait: You might receive a fake email, text message, or social media message that looks incredibly real, perhaps from your bank, a popular online store, or even a colleague. These messages often create a sense of urgency (“Your account has been suspended!”) or offer something tempting (“Claim your gift!”), urging you to click a link. That link redirects you to a fake login page that resembles the real one. When you enter your username and password, the criminals capture that information.
Story Time: John received an urgent email that resembled his online payment service. It said his account had suspicious activity and he needed to log in immediately to verify. He clicked the link, entered his details, and only later realized it was a cleverly disguised phishing attempt when fraudulent charges started appearing. This illustrates important protection tips against social engineering.
5. Malware & Keyloggers: Silent Spies on Your Devices
Some criminals don't need to guess or trick you directly; they can secretly install malicious software on your computer or phone. Malware like keyloggers can silently record everything you type, including your precious passwords.
How it Works: You might unknowingly download an infected file, click on a malicious link, or visit a compromised website. Once installed, a keylogger runs in the background, capturing every keystroke and sending that information back to the attacker. Other malware can even steal saved passwords directly from your web browser.
Your Vulnerability: Not having up-to-date antivirus software and clicking on suspicious links are common ways these silent spies sneak onto your devices. These are critical points for protecting oneself.
Building Your Digital Fortress: Powerful Tips to Protect Oneself from Password Attacks
Now that you understand how the bad guys operate, let’s focus on how you can build an impenetrable digital fortress and protect yourself effectively. These tips will turn you into a digital security pro!
1. Embrace Multi-Factor Authentication (MFA): Your Digital Bodyguard!
If there’s one super-powered security measure you should implement today, it’s Multi-Factor Authentication (MFA). Think of it as adding an extra layer of security to your online accounts. Even if a criminal manages to crack your password, they’ll still need that second verification step to get in.
How it works: After you enter your password, the website or app will ask for a second form of verification, such as a code from an authenticator app on your phone (like Google Authenticator or Authy), a physical security key, or a biometric scan (fingerprint or facial ID).
Action: Enable MFA on every account that offers it, especially your email, banking, social media, and any other important services. For the best protection tips, prioritize using authenticator apps or hardware security keys over SMS-based codes, as those can sometimes be intercepted.
2. Craft Strong & Unique Passwords (or Better Yet, Passphrases!): Quality and Individuality are Key
The foundation of good password security remains using strong, unique passwords for every single online account.
Length Matters Most: Aim for passwords that are at least 12-16 characters long. Longer passwords are significantly harder to crack through brute-force attacks.
Think Passphrases, Not Just Words: Instead of trying to remember a jumble of random characters, create a memorable but unusual phrase. For example, “MyOldBikeLovesSunnyDaysAndPizza!” is much longer and harder to guess than “BikeLove123!”.
Never Reuse Passwords: This is a golden rule! As we learned with credential stuffing, using the same password across multiple sites is like giving criminals a master key to your digital life. This is one of the most critical password tips.
3. Become Best Friends with a Password Manager: Your Secure Digital Vault
Trying to remember dozens of strong, unique passwords is nearly impossible for most people. That’s where a password manager becomes your invaluable ally.
How it Works: A password manager (like 1Password, Bitwarden, Dashlane, or LastPass) generates strong, random, and unique passwords for all your accounts and stores them securely in an encrypted vault. You only need to remember one strong “master password” to access the vault. Most also have convenient features like auto-filling login details.
Action: Research and choose a reputable password manager and start using it today. It’s one of the best protection tips for managing your digital keys.
4. Sharpen Your Phishing Detection Skills: Be a Skeptic!
Your awareness is a crucial defense against phishing and social engineering attacks.
Hover Before You Click: Before clicking any link in an email, text, or social media message, hover your mouse over it (on a computer) or long-press (on a phone) to see the actual web address. Does it look legitimate? If it says “yourbank.com” but the link goes to something like “suspicious-website.ru,” it’s a red flag!
Check Sender Details Carefully: Scrutinize the sender's email address or phone number. Look for subtle misspellings or unusual characters.
Be Wary of Urgent Requests: Phishing attempts often create a sense of urgency or threat to pressure you into acting without thinking.
Go Directly to the Source: If you receive a suspicious message from a company, don’t click the link. Instead, open your web browser and type in the official website address yourself.
Trust Your Gut: If something feels “off” about a message, it probably is. These are essential tips to protect oneself.
5. Keep Your Software Updated: Seal the Security Gaps!
Software updates aren’t just about new features; they often include critical security patches that fix vulnerabilities criminals could exploit to install malware and steal your passwords.
Why it Matters: Outdated software is like having unlocked doors in your digital home. Updates close those doors and strengthen your defenses.
Action: Enable automatic updates for your operating system (Windows, macOS, iOS, Android), web browsers, antivirus software, and all other applications. This is a simple but highly effective protection tip.
6. Be Smart on Public Wi-Fi: Protect Your Data in Transit
Public Wi-Fi networks (like at coffee shops or airports) can be convenient, but they're also often less secure.
The Risk: On an unsecured public Wi-Fi network, criminals might be able to intercept your internet traffic, including the information you enter when logging into websites.
Action: Avoid logging into sensitive accounts (like banking or email) on public Wi-Fi. Consider using a reputable Virtual Private Network (VPN), which encrypts your internet traffic and creates a secure tunnel for your data. This is a valuable protection tip when you’re on the go.
7. Monitor for Data Breaches: Stay Informed, Stay Protected
Even with the best passwords and security habits, data breaches can still happen at the companies and services you use.
Tools to Use: Websites like “Have I Been Pwned?” allow you to enter your email address and see if it has been involved in any known data breaches. Many password managers also offer this feature.
Action: Regularly check if your email address has been compromised. If it has, immediately change the password for that account and any other accounts where you might have used the same password. This proactive step is key to protecting oneself.
Your Digital Safety Starts Now!
Protecting yourself from password attacks doesn’t require you to be a tech expert. By understanding how criminals operate and implementing these practical tips, you can significantly strengthen your online security. It’s about building good habits and using the tools available to create your own unbreakable digital vault.
Take these steps today and empower yourself to navigate the internet with confidence and peace of mind!
Ready to Level Up Your Digital Security?
Don't wait until it's too late! Subscribe to our free weekly cybersecurity newsletter for more easy-to-understand tips, practical advice, and the latest updates on how to protect oneself from online threats.
👉 Click here to subscribe and fortify your digital defenses!














For any concerns, suggestions, feedback, please contact us at support@bryansolidarios.com
© 2025. All rights reserved.
Subscribe here
AI Assistant
AI Content & Licensing Disclosure
All musical tracks and visual media under the "System Failure" project are created using a hybrid of human composition and Advanced Generative AI (Suno v5/v2026 & Image Generation).
Commercial Rights: All tracks hosted here are generated under an active commercial license.
Ownership Note: Per 2026 AI platform terms, while commercial use is granted to Bryan Solidarios, the copyright status of AI-generated outputs is subject to evolving international laws regarding non-human authorship.
Educational Purpose: This content is part of a cybersecurity awareness initiative to demonstrate the intersection of IT, AI, and digital security.