10 Cybersecurity Myths We Need to Stop Believing Now!
The top 10 most common myths in cybersecurity
Bryan Solidarios
8/5/20257 min read


The Digital Ghost Stories: 10 Cybersecurity Myths We Need to Stop Believing Now!
Hey there! Let’s be real for a second. We’ve all told ourselves a little white lie to feel safer online. Things like, “I’m too small to be a target,” or “My antivirus has my back, no problem.” These are our digital ghost stories—comforting tales we tell ourselves to ward off the spooky stuff. The only problem is that these comforting lies are cybersecurity myths that leave the front door wide open to real risks. Today, we're on a mission to debunk these myths. By clarifying these digital misconceptions, you'll feel empowered and confident, not just safe. Let’s get started!
Myth 1: "Hackers only go after big companies or rich people."
This is the digital equivalent of thinking only mansions get robbed. But guess what? A thief looking for an easy score will often target a house with an unlocked window first. Hackers aren't always after a single, massive payday; they’re usually after volume, and you're part of that volume.
The Reality: Small businesses and individuals are the low-hanging fruit. Smaller organizations often lack the advanced security systems that larger companies have, leaving them more vulnerable to cyberattacks. These attacks are automated and designed to reach as many people as possible. A large number of cyberattacks target smaller businesses. They’re simply easier to get into.
The Story: My friend, who runs a small online store, learned this the hard way. He thought his little shop was too insignificant to bother with two-factor authentication. One day, a hacker gained access, not for his store's funds, but to steal customer data and send out thousands of phishing scams under his business’s name. His reputation was on the line, all because of one little myth.
Myth 2: "My Mac can't get a virus."
Oh, if only this were true! This myth has been around since the dawn of Apple. While Macs boast excellent built-in security features, believing they’re invulnerable is like assuming a luxury car is immune to getting a flat tire.
The Reality: Macs can, and do, get viruses and other malware. As Macs have become more popular, they’ve become a more attractive target for cybercriminals. Malware is crafted to be deceptive and can slip past even the most robust built-in defenses.
The Takeaway: The key to protecting against cyber threats isn't about what brand you use, but about how you behave online. Practice the same good habits on your Mac that you would on any other device. This means staying cautious, using a password manager, and ensuring all your software is updated and secure.
Myth 3: "Antivirus software makes me invincible."
This is like hiring a security guard for your front door and then leaving all the other windows and doors wide open. Antivirus software is essential, but it's just one piece of the puzzle.
The Reality: Antivirus primarily defends against known threats. It’s not a magic shield against brand-new attacks (called zero-day exploits), and it certainly won't stop you from falling for a convincing phishing scam.
The Takeaway: Effective online security involves implementing multiple layers of protection. You need a firewall, a strong password, Multi-Factor Authentication (MFA), and, most importantly, your common sense. Think of it as a whole security system, not just a single lock.
Myth 4: "My password is good enough."
We've all been guilty of this: using a password that’s just a little too easy to remember, or even worse, reusing it across multiple sites. A strong password is a great first step, but it’s not the whole journey.
The Reality: Passwords can be stolen in data breaches, or they can be tricked out of you through a clever phishing scam. Once your password is leaked, it’s out there for good.
The Game-Changer: This is where Multi-Factor Authentication (MFA) comes in. MFA adds an extra layer of security by requiring a second step, like a code from your phone or a fingerprint scan, to verify your identity. Even if a hacker gets your password, they’re completely blocked without that second factor. It’s the ultimate security upgrade!
Myth 5: "I'll know if I've been hacked because my computer will be slow or have pop-ups."
Wouldn't that be convenient? The truth is, the most successful cybercriminals don't want to be noticed. They want to be a silent ghost in your machine, quietly collecting data.
The Reality: A hacker can lurk in your system for months, siphoning off your personal information, bank details, and other private data without a single slowdown or pop-up. They're patient and stealthy.
The Proactive Move: Don't wait for a warning sign. Make it a habit to review your bank and credit card statements for anything suspicious. Use free tools like "Have I Been Pwned?" to check if your email has been involved in a data breach. Staying proactive is your best protection.
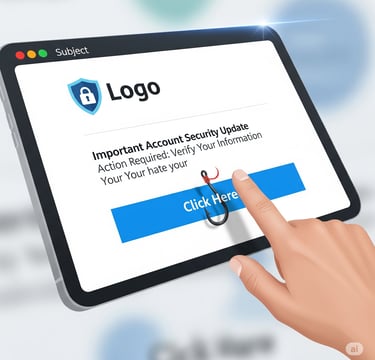
Myth 6: "Phishing emails are easy to spot."
Oh, how we wish this were true! Gone are the days of poorly spelled emails from long-lost relatives leaving you a fortune. Modern phishing scams are highly convincing.
The Reality: Phishers nowadays use convincing company logos, flawless web designs, and even gather publicly available details like your name or job title to make their emails appear credible. They often create a sense of urgency to trick you into clicking without hesitation.
The Expert Tip: Never click a link in a suspicious email. The top phishing tip for savvy users is to hover your mouse over a link to check its destination. If you’re still unsure, type the official website address directly into your browser.
Myth 7: "I’ve deleted a file, so it’s gone for good."
This is a favorite digital ghost story. When you hit delete, your computer doesn’t erase the data. It just marks that space on your hard drive as "available for new data."
The Reality: Without reliable data wiping tools, a cybercriminal who gains access to your device could use file recovery software to bring back files you thought were deleted. Old documents, photos, and financial records may still be available, waiting to be recovered.
The Takeaway: If you're selling or getting rid of a device, you need to perform a factory reset or use specialized data destruction software. This is the only way to ensure your deleted sensitive information stays deleted.
Myth 8: "Cybersecurity is the IT team’s problem."
This myth is a collective sigh of relief for many employees, but it's a dangerous one. While your IT department provides the tools and sets the rules, everyone is on the frontline of your security.
The Reality: The "human element" is the single biggest cause of data breaches. One employee falling for a phishing scam or using a weak password can be the single point of failure that compromises an entire company's network.
The Collective Mission: Think of it like a team sport. Everyone has to do their part. By being vigilant and following simple online security tips, you become the most powerful defense against cybersecurity risks.
Myth 9: "More security software means better security."
This one sounds logical, right? Stacking multiple security tools can create more issues than it fixes. It's like installing five separate security systems in your house that can't communicate with each other.
The Reality: Too many tools can conflict with one another, slow down your device, and, ironically, create unexpected gaps in your defenses.
The Right Approach: Focus on a cohesive, layered security strategy. Use one reputable security suite that works well together, and prioritize foundational practices like MFA, a password manager, and keeping all your software updated and secured.
Myth 10: "Backups aren’t necessary, I use the cloud."
The cloud is an amazing tool, but it's not a magical safety net for all your data. A single point of failure, whether caused by a breach or accidental deletion, can still result in data loss.
The Reality: Even though cloud providers offer excellent security, a data breach on your side can still put your cloud-stored data at risk. Plus, ransomware can encrypt your files and then sync those encrypted files to the cloud, rendering your backups useless.
The Smart Plan: Stick to the "3-2-1" rule: keep three copies of your data, stored on two different types of media, with one copy kept off-site (like in the cloud or on a separate hard drive). This backup strategy helps ensure you can always recover your files.
Ready to Be a Digital Mythbuster?
Exposing these cybersecurity myths is a big move toward protecting your digital life. Keep in mind, real security comes from taking informed action, not relying on blind trust.
So, go forth, enable MFA, update your software, and be a savvy digital citizen!
Want More Brilliant Insights and Exclusive Tips?
Join our free, fun, and jargon-free cybersecurity newsletter! We'll send you the latest online security tips and help you stay a step ahead of the digital ghost stories.
















For any concerns, suggestions, feedback, please contact us at support@bryansolidarios.com
© 2025. All rights reserved.
Subscribe here
AI Assistant
AI Content & Licensing Disclosure
All musical tracks and visual media under the "System Failure" project are created using a hybrid of human composition and Advanced Generative AI (Suno v5/v2026 & Image Generation).
Commercial Rights: All tracks hosted here are generated under an active commercial license.
Ownership Note: Per 2026 AI platform terms, while commercial use is granted to Bryan Solidarios, the copyright status of AI-generated outputs is subject to evolving international laws regarding non-human authorship.
Educational Purpose: This content is part of a cybersecurity awareness initiative to demonstrate the intersection of IT, AI, and digital security.